“One of these days, I’m going to write a book called, ‘The Basics.’ It’s going to be a compendium of the essential tech bits that you just assume everyone knows–but you’re wrong.
“(I’ll never forget watching a book editor at a publishing house painstakingly drag across a word in a word processor to select it. After 10 minutes of this, I couldn’t stand it. ‘Why don’t you just double-click the word?’ She had no clue you could do that!)”
Many readers chimed in with other “basics” that they assumed every computer user knew–but soon discovered that what’s common knowledge isn’t the same as universal knowledge.
I’m sure the basics could fill a book, but here are a few to get you started. All of these are things that certain friends, family or coworkers, over the years, did *not* know. Clip, save and pass along to…well, you know who they are.
* You can double-click a word to highlight it in any document, e-mail or Web page.
* When you get an e-mail message from eBay or your bank, claiming that you have an account problem or a question from a buyer, it’s probably a “phishing scam” intended to trick you into typing your password. Don’t click the link in the message. If in doubt, go into your browser and type “www.ebay.com” (or whatever) manually.
* Nobody, but nobody, is going to give you half of $80 million to help them liberate the funds of a deceased millionaire…from Nigeria or anywhere else.
* You can hide all windows, revealing only what’s on the computer desktop, with one keystroke: hit the Windows key and “D” simultaneously in Windows, or press F11 on Macs (on recent Mac laptops, Command+F3; Command is the key with the cloverleaf logo). That’s great when you want examine or delete something you’ve just downloaded to the desktop, for example. Press the keystroke again to return to what you were doing.
* You can enlarge the text on any Web page. In Windows, press Ctrl and the plus or minus keys (for bigger or smaller fonts); on the Mac, it’s the Command key and plus or minus.
* You can also enlarge the entire Web page or document by pressing the Control key as you turn the wheel on top of your mouse. On the Mac, this enlarges the entire screen image.
* The number of megapixels does not determine a camera’s picture quality; that’s a marketing myth. The sensor size is far more important. (Use Google to find it. For example, search for “sensor size Nikon D90.”)
* On most cellphones, press the Send key to open up a list of recent calls. Instead of manually dialing, you can return a call by highlighting one of these calls and pressing Send again.
* When someone sends you some shocking e-mail and suggests that you pass it on, don’t. At least not until you’ve first confirmed its truth at snopes.com, the Internet’s authority on e-mailed myths. This includes get-rich schemes, Microsoft/AOL cash giveaways, and–especially lately–nutty scare-tactic messages about our Presidential candidates.
* You can tap the Space bar to scroll down on a Web page one screenful. Add the Shift key to scroll back up.
* When you’re filling in the boxes on a Web page (like City, State, Zip), you can press the Tab key to jump from box to box, rather than clicking. Add the Shift key to jump through the boxes backwards.
* You can adjust the size and position of any window on your computer. Drag the top strip to move it; drag the lower-right corner (Mac) or any edge (Windows) to resize it.
* Forcing the camera’s flash to go off prevents silhouetted, too-dark faces when you’re outdoors.
* When you’re searching for something on the Web using, say, Google, put quotes around phrases that must be searched together. For example, if you put quotes around “electric curtains,” Google won’t waste your time finding one set of Web pages containing the word “electric” and another set containing the word “curtains.”
* You can use Google to do math for you. Just type the equation, like 23*7+15/3=, and hit Enter.
* Oh, yeah: on the computer, * means “times” and / means “divided by.”
* If you can’t find some obvious command, like Delete in a photo program, try clicking using the right-side mouse button. (On the Mac, you can Control-click instead.)
* Google is also a units-of-measurement and currency converter. Type “teaspoons in 1.3 gallons,” for example, or “euros in 17 dollars.” Click Search to see the answer.
* You can open the Start menu by tapping the key with the Windows logo on it.
* You can switch from one open program to the next by pressing Alt+Tab (Windows) or Command-Tab (Mac).
* You generally can’t send someone more than a couple of full-size digital photos as an e-mail attachment; those files are too big, and they’ll bounce back to you. (Instead, use iPhoto or Picasa–photo-organizing programs that can automatically scale down photos in the process of e-mailing them.)
* Whatever technology you buy today will be obsolete soon, but you can avoid heartache by learning the cycles. New iPods come out every September. New digital cameras come out in February and October.
* Just putting something into the Trash or the Recycle Bin doesn’t actually delete it. You then have to *empty* the Trash or Recycle Bin. (Once a year, I hear about somebody whose hard drive is full, despite having practically no files. It’s because over the years, they’ve put 79 gigabytes’ worth of stuff in the Recycle Bin and never emptied it.)
* You don’t have to type “http://www” into your Web browser. Just type the remainder: “nytimes.com” or “dilbert.com,” for example. (In the Safari browser, you can even leave off the “.com” part.)
* On the iPhone, hit the Space bar twice at the end of a sentence. You get a period, a space, and a capitalized letter at the beginning of the next word.
* Come up with an automated backup system for your computer. There’s no misery quite like the sick feeling of having lost chunks of your life because you didn’t have a safety copy.

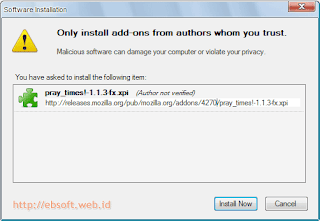
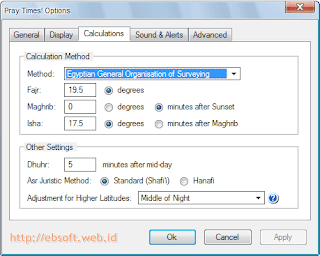
 For those of you who frequent browsing (exploring) the virtual world with Mozilla Firefox, so if there is no reminder, could forget the time when prayer has been entered. Among the benefits of Firefox is support Add-ons (additional functions) that there are so many. One of them is a prayer reminder.
For those of you who frequent browsing (exploring) the virtual world with Mozilla Firefox, so if there is no reminder, could forget the time when prayer has been entered. Among the benefits of Firefox is support Add-ons (additional functions) that there are so many. One of them is a prayer reminder.